高等UNIX程式設計:作業二
0x00 前言
0x01 作業描述
本次作業主要為練習 library injection 和 API hijacking
List of Candidate Programs
- lftp : web;
- links : web;
- curl : web;
- Other networked client programs available on CS Linux workstations.
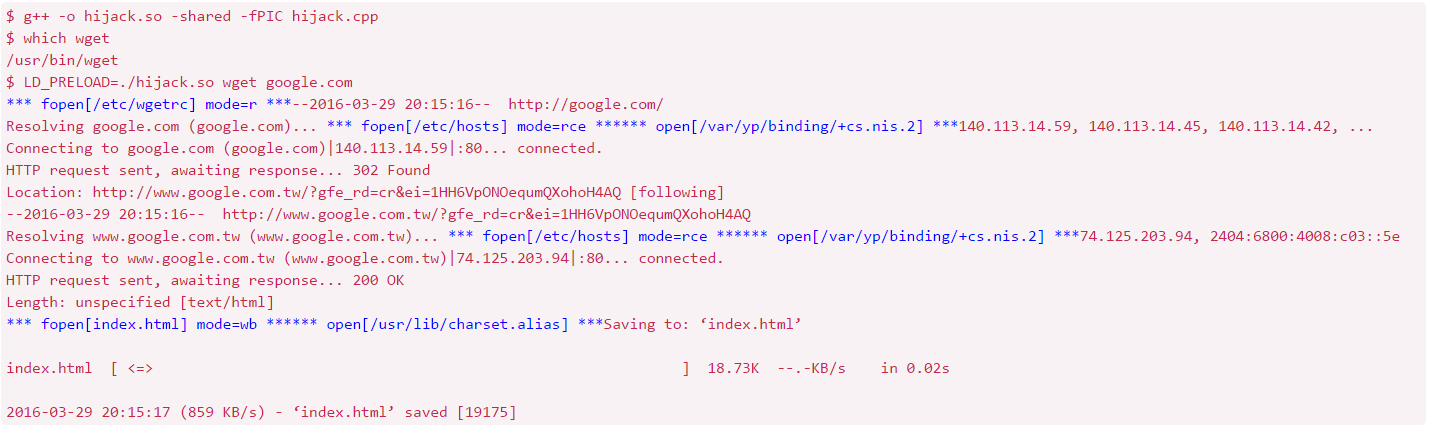
從上方清單中選擇一個 networked client programs,使用 LD_PRELOAD 的方式將自己寫的作業 inject 進去而取得一些程式資訊,將取得的資訊記錄在一個或多個檔案
作業要求需要取得的資訊如下:
- 涉及 file and directory 操作,如 creation, open, read, write, rename, deletion…等,這些動作涉及的參數也要一併紀錄下來。這是作業最低要求
- client program 連線到的 IP address or host name
- client program 和 server 間的 data exchanged,連線可能是加密的,所以機加密的 APIs 都要 hijack
- 其它自己認為有用的資訊
作業需要自己編譯成 shared object
作業會從 正確性、完整性、hijack 的特徵數和難度四個項目評分
0x02 範例程式
0x03 作業提示
Most of involved API functions are from the standard C library (e.g., libc.so.6 on Linux).
For hijacking encrypted connections,
a client program may work with OpenSSL (e.g., libcrypto.so.1.0.0 and libssl.so.1.0.0) or GNU TLS library (e.g., libgnutls.so.26).
You may read the source codes of your target program first and check how your target program calls the mentioned libraries.
You can then implement your homework based on your observations.
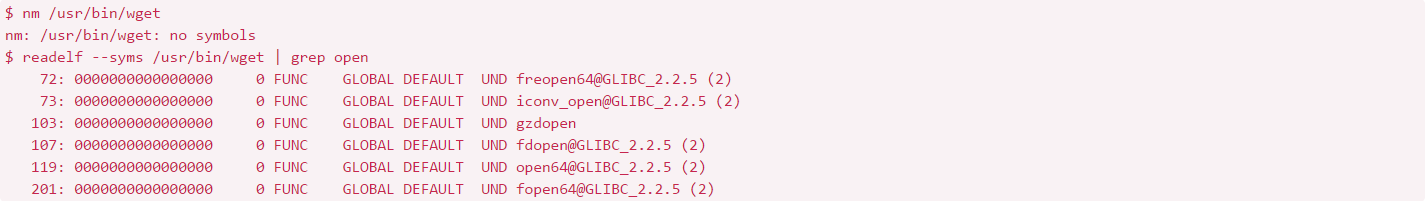
We have mentioned that you are not able to see the symbols if the symbols were stripped using the strip command. However,
you may consider working with the readelf command. For example, we can check the symbols that are unknown to the binary:
Alternatively, you may consider using nm -D to read symbols. Basically we have two different symbol tables.
One is the regular symbol table and the other is dynamic symbol table. The one removed by strip is the regular symbol table.
So you will need to work with nm -D or readelf --syms to read the dynamic symbol table.